What is CVSS?
CVSS stands for Common Vulnerability Scoring System. It is a way to measure and communicate the severity of software vulnerabilities.
CVSS gives every vulnerability a score from 0 to 10. The higher the score, the bigger the risk. It enables IT organizations to prioritize vulnerabilities for remediation based on the potential damage they represent to their environments. Furthermore, it also provides a standardized method for vulnerability bulletin providers to describe the characteristics and impacts of vulnerabilities in their products.
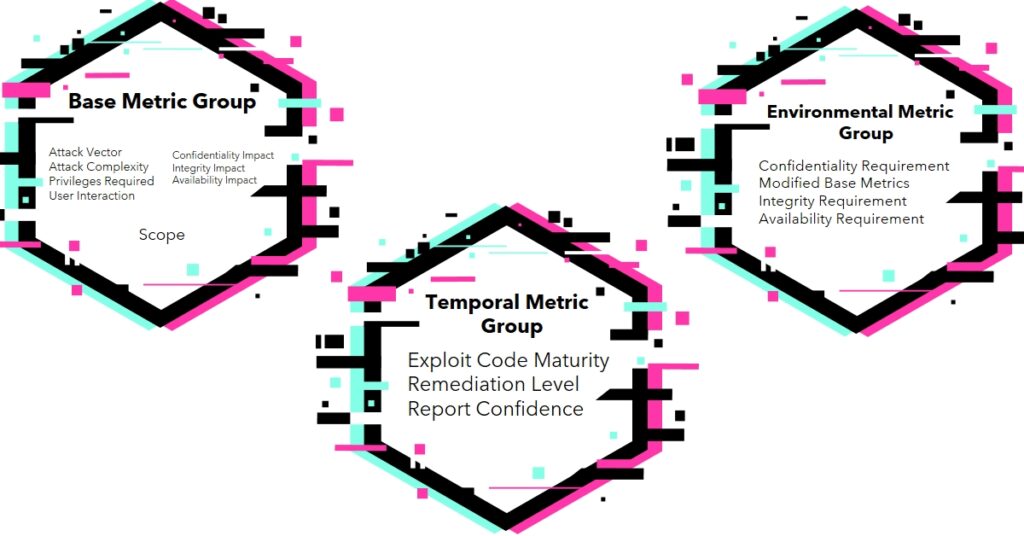
CVSS splits vulnerabilities into 3 groups:
- Base – Built-in traits of a weakness. These don’t change over time.
- Temporal – Traits that change over time, like fixes becoming available.
- Environmental – Traits specific to a company’s systems and priorities.
The Base Metrics
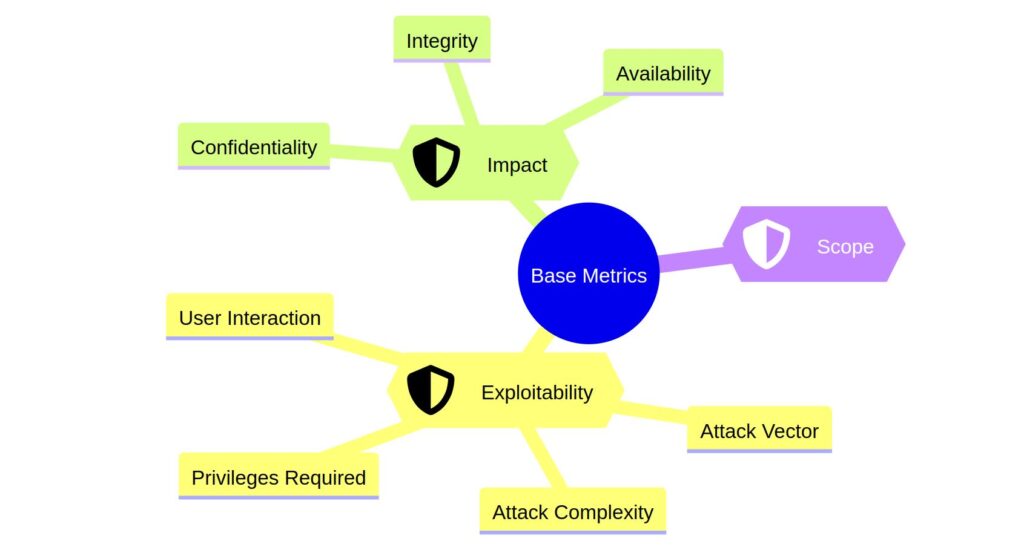
The Base metrics represent the inherent qualities of a vulnerability that are constant over time and across environments. They are composed of two sets – Exploitability and Impact.
Exploitability Metrics
The Exploitability metrics show how easy a vulnerability can be exploited. They include:
- Attack Vector (AV) – Reflects the context by which vulnerability exploitation is possible. Remote vulnerabilities have higher scores.
- Attack Complexity (AC) – Describes the conditions beyond the attacker’s control that must exist to exploit the vulnerability. The lower the required complexity, the higher the score.
- Privileges Required (PR) – Measures the level of privileges an attacker must have before successfully exploiting the vulnerability. Higher privileges result in a lower score.
- User Interaction (UI) – Captures the requirement for a user, other than the attacker, to participate in the successful compromise of the vulnerable component. No user interaction results in a higher score.
Impact Metrics
The Impact metrics show how much damage a successful hack could cause. They measure loss of Confidentiality, Integrity, and Availability:
- Confidentiality (C) – Measures the impact to data confidentiality. Complete loss of confidentiality leads to a higher score.
- Integrity (I) – Measures the impact to data integrity. Complete loss of integrity results in a higher score.
- Availability (A) – Measures the impact to service availability. A total denial of service leads to a higher score.
Scope Metric
The Scope metric measures whether a vulnerability in one component can impact resources beyond that component’s security boundaries.
A security authority defines and controls access to certain resources like files or memory. All subjects (users, processes) and objects (resources) under one security authority are considered to be in the same security scope.
If a vulnerability in one component can affect resources in a different security scope, then a scope change occurs. This means the impact of the vulnerability breaches a security boundary. For example, a vulnerability in an application should not be able to impact resources controlled by the operating system. If it can, that is considered a scope change.
The Base Score is higher when a scope change happens. This is because a scope change indicates the vulnerability bypasses security boundaries and can impact more resources.
The Base Score
The Exploitability and Impact metrics produce sub-scores that are used to calculate the Base Score, which ranges from 0 to 10, with 10 being most severe. The Base Score represents the intrinsic qualities of a vulnerability that are constant over time and across environments.
Temporal Metrics
The Temporal metrics reflect the characteristics of a vulnerability that change over time. They include:
- Exploit Code Maturity (E) – Measures the likelihood of a vulnerability being attacked based on the current state of exploit techniques or code availability. The more easily a vulnerability can be exploited, the higher this metric’s value.
- Remediation Level (RL) – Captures the availability of official fixes or workarounds. The less mature and permanent the fix, the higher the score.
- Report Confidence (RC) – Measures the degree of confidence in the vulnerability details and existence. More certainty results in a higher score.
The Temporal metrics modify the Base Score to reflect changes to a vulnerability’s severity over time.
Environmental Metrics
The Environmental metrics enable the analyst to customize the score depending on the importance of the affected IT asset to a user’s organization.
- Confidentiality Requirement (CR) – Measures the impact to confidentiality of a successful exploit based on the importance of data confidentiality to the organization.
- Integrity Requirement (IR) – Measures the impact to integrity based on the importance of data integrity to the organization.
- Availability Requirement (AR) – Measures the impact to availability based on the importance of service availability to the organization.
Higher requirements result in a greater impact and higher Environmental Score.
The Environmental metrics allow organizations to tailor CVSS scores to their unique environments and priorities.
Scoring a Vulnerability
Scoring CVSS metrics produces a vector string that communicates the characteristics of a vulnerability in a standardized form, as well as a numeric score between 0 and 10.
Rating Scale
In certain scenarios, having a text-based representation of the numeric Base, Temporal, and Environmental scores proves beneficial. You can match the scores with the ratings in the Table. For instance, a CVSS Base Score of 7.0 is labeled as High severity.
However, using these ratings is your choice. There’s no rule saying you must include them when sharing CVSS scores. They’re there to assist organizations in evaluating and prioritizing vulnerability management.
| Rating | CVSS Score |
|---|---|
| None | 0.0 |
| Low | 0.1 – 3.9 |
| Medium | 4.0 – 6.9 |
| High | 7.0 – 8.9 |
| Critical | 9.0 – 10.0 |
Vector String
The CVSS v3.1 vector string is a text version of CVSS metrics. It shows the metrics in a short and structured way.
The vector string starts with “CVSS:3.1”. This shows the CVSS version. Then each metric is listed separated by “/”. Metrics are written in shorthand using the name and value abbreviations defined earlier. For example “AV:N” for Attack Vector = Network. All Base metrics are mandatory. Temporal and Environmental metrics are optional. The same metric can’t be included twice.
Example vector string for CVE-2023-6000:
AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:HReal-world Examples
Unauthenticated Remote Code Execution:
| Vector |
AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| Base Score | 9.8 |
| Exploitability Score: 3.9 Attack Vector (AV): Network Attack Complexity (AC): Low Privileges Required (PR): None User Interaction (UI): None Impact Score: 5.9 Scope (S): Unchanged |
|
| Temporal Score | N/A |
| Environmental Score | N/A |
| Overall CVSS Score | 9.8 CRITICAL |
Learn more from CVSS Calculator – nvd.nist.gov
| Vector |
AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
| Base Score | 8.8 |
| Exploitability Score: 2.8 Attack Vector (AV): Network Attack Complexity (AC): Low Privileges Required (PR): None User Interaction (UI): Required Impact Score: 5.9 Scope (S): Unchanged |
|
| Temporal Score | N/A |
| Environmental Score | N/A |
| Overall CVSS Score | 8.8 HIGH |
Learn more from CVSS Calculator – nvd.nist.gov
Read More
For detailed and technical information please refer to the official CVSS v3.1: Specification Document.
Frequently Asked Questions
[Q] What is the main benefit of CVSS?
CVSS provides a standardized way to capture the principal characteristics of vulnerabilities and consistently score them on a scale from 0 to 10. This simplifies comparing and prioritizing vulnerabilities. Companies can focus fixes on threats posing the greatest danger to their business.
[Q] How can I use CVSS as part of a vulnerability management program?
The CVSS scores and vectors can be used to consistently and objectively prioritize vulnerabilities for remediation based on threat levels across an environment.
[Q] How does CVSS version 3.1 differ from its predecessor?
CVSS version 3.1 brings refinements in scoring guidance, updates to metric values, and introduces the Extensions Framework. The changes aim to enhance clarity, consistency, and applicability across diverse scenarios.

